Introduction
Dispatcher Paragon Cloud server has a possibility to enable denial of service (DoS) filtering to prevent the system from being overloaded by excessive amounts of requests. DoS filter can be enabled for on-premise primary server by editing the configuration file: /opt/DispatcherParagon/conf/application.conf.
DoS filter configuration
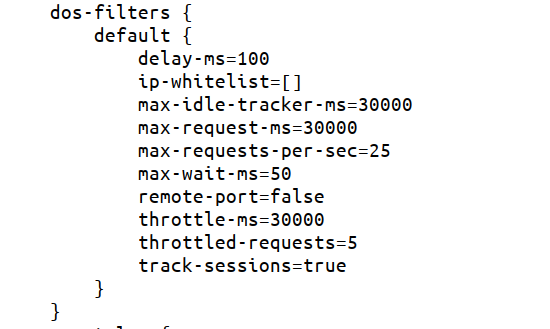
Multiple DoS filters can be defined under app.dos-filters section in the application configuration file. By default there is one filter defined called default:
To activate the particular DoS filter it must be specified in the dos-filter parameter under web section:
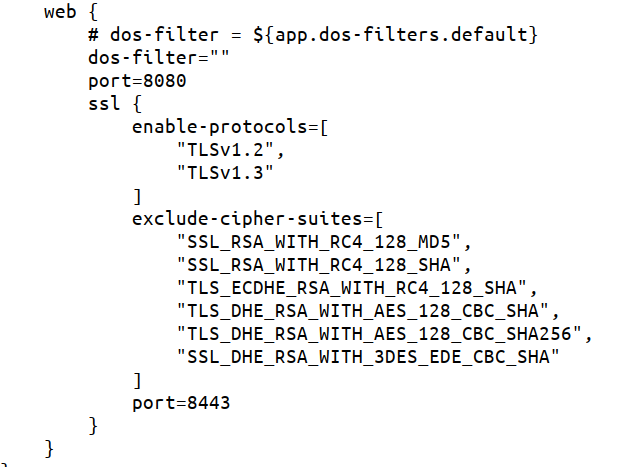
Comment out the dos-filter = "" line (add the # sign) and uncomment the dos-filter = ${app.dos-filters.default} (remove the # sign).
Save the file and restart the server with systemctl restart safeq-cloud-server command.
DoS filter parameters
The following parameters control the behavior of the filter:
-
max-requests-per-sec– Maximum number of requests from a connection per second. Requests in excess of this are first delayed, then throttled. Default is 25. -
delay-ms– Delay imposed on all requests over the rate limit, before they are considered at all: 100 (ms) = Default, -1 = Reject request, 0 = No delay -
max-wait-ms– Length of time, in ms, to blocking wait for the throttle semaphore. Default is 50 ms. -
throttled-requests– Number of requests over the rate limit able to be considered at once. Default is 5. -
throttle-ms– Length of time, in ms, to async wait for semaphore. Default is 30000. -
max-request-ms– Length of time, in ms, to allow the request to run. Default is 30000. -
max-idle-tracker-ms– Length of time, in ms, to keep track of request rates for a connection, before deciding that the user has gone away, and discarding it. Default is 30000. -
track-sessions– If true, usage rate is tracked by session if a session exists. Defaults to true. -
remote-port– If true and session tracking is not used, then rate is tracked by IP and port (effectively connection). Defaults to false. -
ip-whitelist– A comma-separated list of IP addresses that will not be rate limited.